Basic knowledge Security Aspects of RFID
Wonder why RFID is so widespread in the authentication, authorization and access control of people and products?
This white paper provides answers in plain language.
Get your exclusive whitepaper.
From baggage tracking to Industry 4.0, the implementation of RFID technologies is increasing rapidly. With the increasing use of RFID for object and personal identification, the demands on data security are growing. In this white paper, you will learn how to deal with the security dynamics of everyday use and legal requirements. It also presents approaches for holistic security concepts, so you can define your protection goals and achieve them through intelligent implementation.
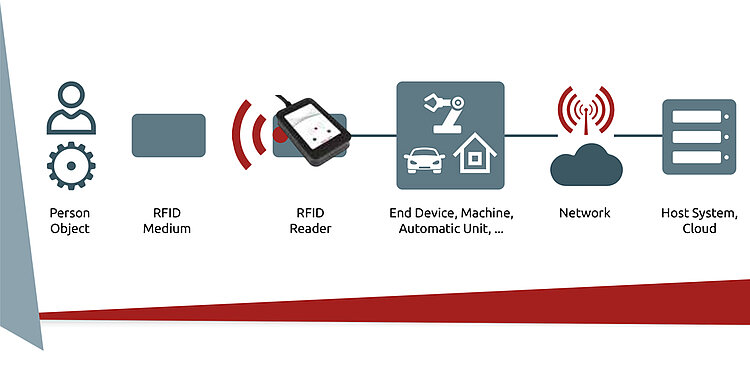
For years, there have been controversial security discussions when it comes to generating and storing data. Nevertheless, some industries have still not made this aspect a top priority. However, it is absolutely necessary to be proactive here. Bring your knowledge up to date with our whitepaper. Learn from these explanations of protection concepts and threat scenarios so you can make your corporate security strategy future-proof.