Is it Time for Your Organization to Implement Zero Trust?
“Zero Trust” is one of the biggest buzzwords in cybersecurity right now. But what exactly is it, and what does it mean for your organization? Here’s what you need to know and how ELATEC can help.
The Evolving Cybersecurity Landscape
The security landscape has changed significantly over the last decade, and many of these changes are accelerating. These are just a few of the shifts the industry has seen recently.
- More people are working remotely and logging into company assets from home or on the road. Instead of coming together in a single home office to work, people are accessing network assets from outside, unsecured locations and working with teams scattered all over the globe.
-
Cloud computing:
There has been a proliferation of cloud-based applications that are now considered essential. These include sales and customer management software, team collaboration programs, and numerous other business systems—many of which house protected data. -
Digital data explosion:
Hand-in-hand with cloud computing, we’ve seen a massive increase in the volume and type of data that companies handle in digital form. That includes intellectual property, business plans, financials, customer data, employee data and other sensitive information, some of which may be subject to strict privacy laws and regulations. -
Device proliferation:
Most people are now accessing the company network with multiple devices, adding smartphones and tablets to their traditional laptops or desktops as endpoint devices. A growing number of these devices are personally owned rather than company owned. -
Threat landscape:
All these changes have significantly expanded the threat landscape: more data, more devices, more people logging in from outside the network, and more information stored on or transmitted through the cloud. This adds up to many more opportunities for bad actors, whether from inside or outside the organization. At the same time, hackers have become much more sophisticated, using advanced tactics ranging from spear phishing to steal credentials of high-status users to machine learning to crack passwords or decode encrypted data.
For decades, organizations have relied on technologies such as firewalls and VPNs (Virtual Private Networks) to protect data and applications housed on the company network. This “perimeter defense” or “castle-and-moat” approach assumes that a person, device or application that is operating inside the protected network can, by default, be trusted. But in today’s complex cybersecurity landscape, this is no longer a safe assumption. That’s why many private companies and government agencies are moving away from “castle-and-moat” to a new security framework: Zero Trust.
What Is Zero Trust?
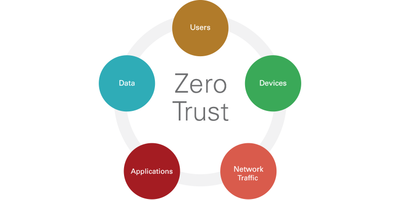
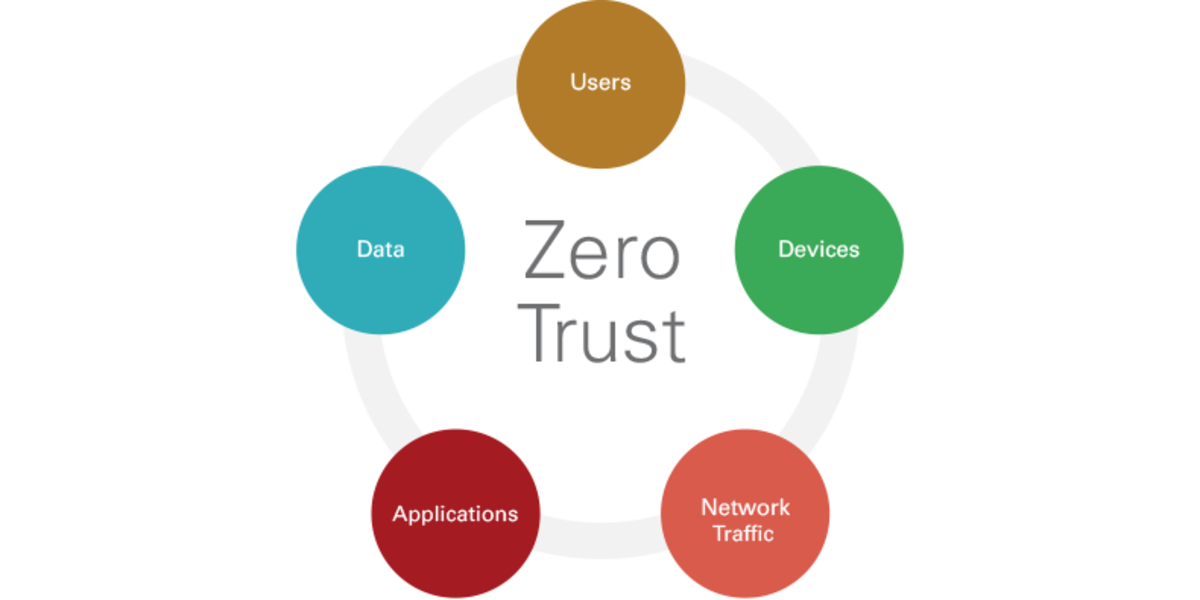
What does Zero Trust mean? In essence, a Zero Trust environment is one in which every user, device and application is verified each and every time they request access to a file, system or service—even if they are already logged into the network. Zero Trust does not make a distinction between users inside or outside the network. Instead, it continually reverifies everyone, no matter where they are located.
Some of the core principles of Zero Trust include the following.
- “Never trust; always verify.” This is the essence of Zero Trust, and it applies to people, devices and applications. Each time access to a network asset or application is requested, the requester must be verified to ensure that 1) they are who/what they say they are, and 2) they have authorization to access the asset requested.
- Principle of least privilege: In addition to verification, Zero Trust demands that requesters be granted the least amount of access for the smallest amount of time required to perform their function. This principle limits opportunities for bad actors to move laterally once inside the network to pivot into areas where they do not belong.
- Limit impacts: A Zero Trust environment is also built to limit the potential impact if an attack should occur. Organizations should have a plan in place that will allow them to quickly detect and respond to unusual activity that indicates a potential breach. Other strategies include micro-segmentation of the network to limit the places an attacker can go once inside.
The Zero Trust Model is a cybersecurity philosophy, not a specific technology. But it does rely on technologies to make it work. Zero Trust Network Access (ZTNA) software manages the continual verification process. When a user or device requests access to an asset or service on the network, ZTNA goes through the verification process to ensure that their identity can be confirmed and they are authorized to access the asset requested—each time a new request is made. This is in contrast to traditional firewall models, which open up access to all assets a user or device is authorized for with a single session login.
Zero Trust and User Authentication
User authentication is at the very heart of Zero Trust architecture. The ZTNA software sits on the back end, moderating access between the user/device and the network assets. It must be paired with a front-end system for user identification. This could mean simply entering a username and password when logging into a device. However, these types of user credentials are easily compromised either through user carelessness, successful phishing attacks, or by hacking into systems where passwords are stored. Stronger systems for user authentication, including multi-factor authentication, are recommended for a secure Zero Trust environment.
This can be easily accomplished using technologies such as radio-frequency identification (RFID) or smartphone-based systems using Near-field Communication (NFC) or Bluetooth® Low Energy (BLE). These systems can be used alone or as part of a multi-factor authentication protocol. For example, an RFID reader can be plugged into a device via USB for PC Logon. The employee must have their ID badge or smartphone with their digital credentials to log into the computer. For multi-factor authentication, the system may require both a password and the ID badge or digital credential. Multi-factor authentication may also be achieved by using biometrics built into the smartphone in addition to the mobile credential.
THE ELATEC NEWSLETTER Your authentication update
As a frequent reader, you will always be up to date with the latest information on the topic of authentication, know the current trends and receive valuable tips. By signing up to our newsletter, we will make sure you won't miss any new blog articles ever again. And on top, you get even more exciting news on our products, events and industry trends.